Traditional security models relied heavily on the network perimeter, trusting internal entities while distrusting external ones. The advent of cloud services, mobile workforces, and IoT devices has rendered this perimeter obsolete. Zero Trust addresses this new reality by advocating the principle of “never trust, always verify.”
In the context of cloud-native 5G, the network’s expanded connectivity significantly increases the attack surface. Zero Trust counters this threat by enforcing continuous verification and authentication of all users, devices, and services, irrespective of location.
Understanding Zero Trust 5G Security
Traditional security models relied heavily on the network perimeter—trusting internal entities while distrusting external ones. The advent of cloud services, mobile workforces, and IoT devices has rendered this perimeter obsolete. Zero Trust addresses this new reality by advocating the principle of “never trust, always verify.”
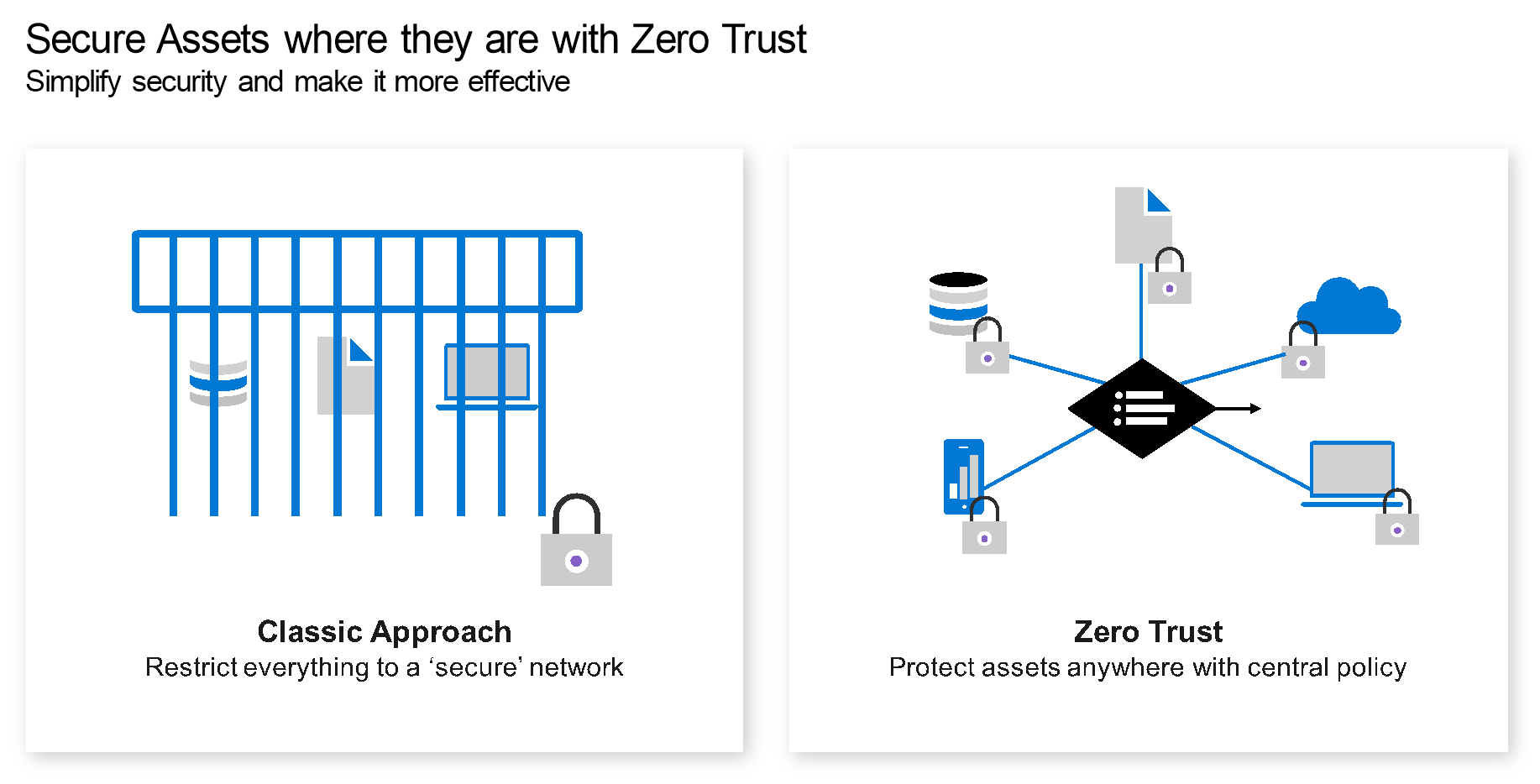
In the context of cloud-native 5G, the network’s expanded connectivity significantly increases the attack surface. Zero Trust counters this threat by enforcing continuous verification and authentication of all users, devices, and services, irrespective of location.
Essential Components of Zero Trust 5G for Cloud-Native applications
To effectively secure a 5G-enabled environment, your Zero Trust strategy should include:
- Continuous Authentication and Authorization: Frequent verification based on user behavior, context, and real-time risk assessments.
- End-to-End Governance: Comprehensive oversight and control extending from on-premises systems through to cloud infrastructure.
- Dynamic Policy Enforcement: Real-time adjustments to access permissions based on threat intelligence and changing contexts.
- Enhanced Monitoring and Threat Detection: Utilizing advanced analytics to proactively detect anomalies and breaches.
When executed properly, these components collectively enhance security resilience while maintaining operational flexibility.
The Importance of the Human Element
Many Zero Trust implementations neglect the human factor, focusing solely on technological solutions. At Origo, we recognize this critical oversight can lead to implementation difficulties, user resistance, and unintended vulnerabilities.
Security systems that impede user productivity inadvertently encourage workarounds, introducing new security risks. Effective security must enhance rather than hinder the user experience.
Origo’s Human-Centered Approach
Our strategy integrates human-centric principles to drive successful Zero Trust implementations:
- Simplified User Experiences: Leveraging biometrics, single sign-on, and frictionless authentication technologies.
- Contextual Security: Adjusting security measures dynamically based on evaluated risks, ensuring rigorous security only when necessary.
- User Education: Tailored training programs designed to foster understanding and encourage adherence to security practices.
By placing people at the core of our security solutions, Origo ensures robust security without compromising user satisfaction or productivity.
Origo’s Expertise in Enterprise and 5G Infrastructure
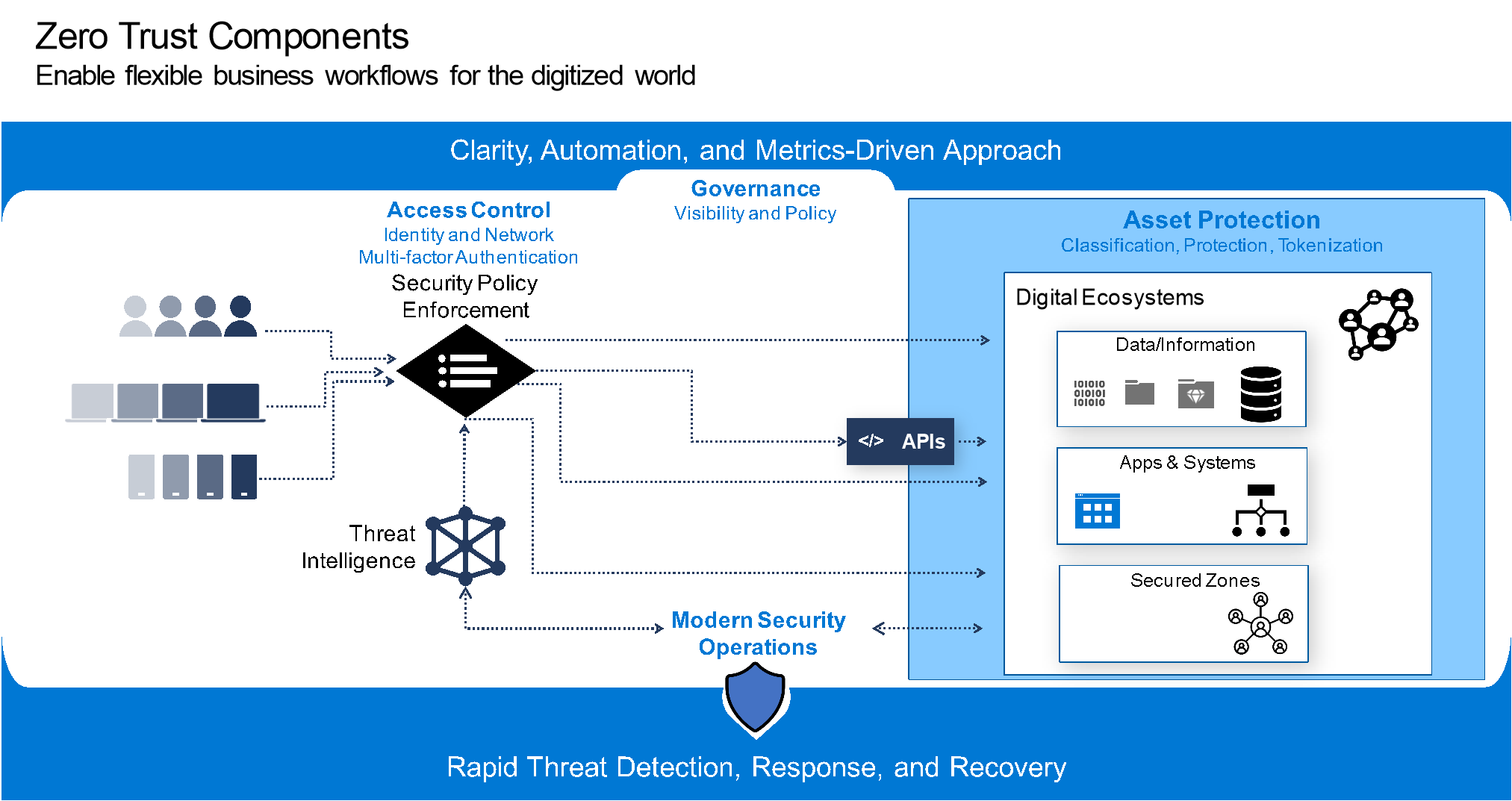
Origo possesses extensive experience delivering tailored security solutions specifically designed for enterprise environments and advanced 5G infrastructure. Our specialists collaborate closely with enterprises to:
- Develop Zero Trust strategies aligned with business objectives, risk tolerance, and compliance requirements.
- Provide specialized expertise in cloud-native security, identity management, vulnerability management, and security orchestration.
- Seamlessly integrate cutting-edge AI and machine learning technologies into security operations, enhancing threat detection and response.
Leveraging AI and ML for Enhanced Security
Origo incorporates AI and ML capabilities into your Zero Trust framework, significantly bolstering your security posture through:
- Behavioral Analytics: Detecting deviations from baseline user behaviors that might indicate security threats.
- Threat Intelligence: Integrating data from diverse sources to anticipate and mitigate attacks.
- Automated Response: Swiftly containing threats with minimal disruption to legitimate operations.
Our approach ensures that advanced technologies empower users rather than creating new obstacles.
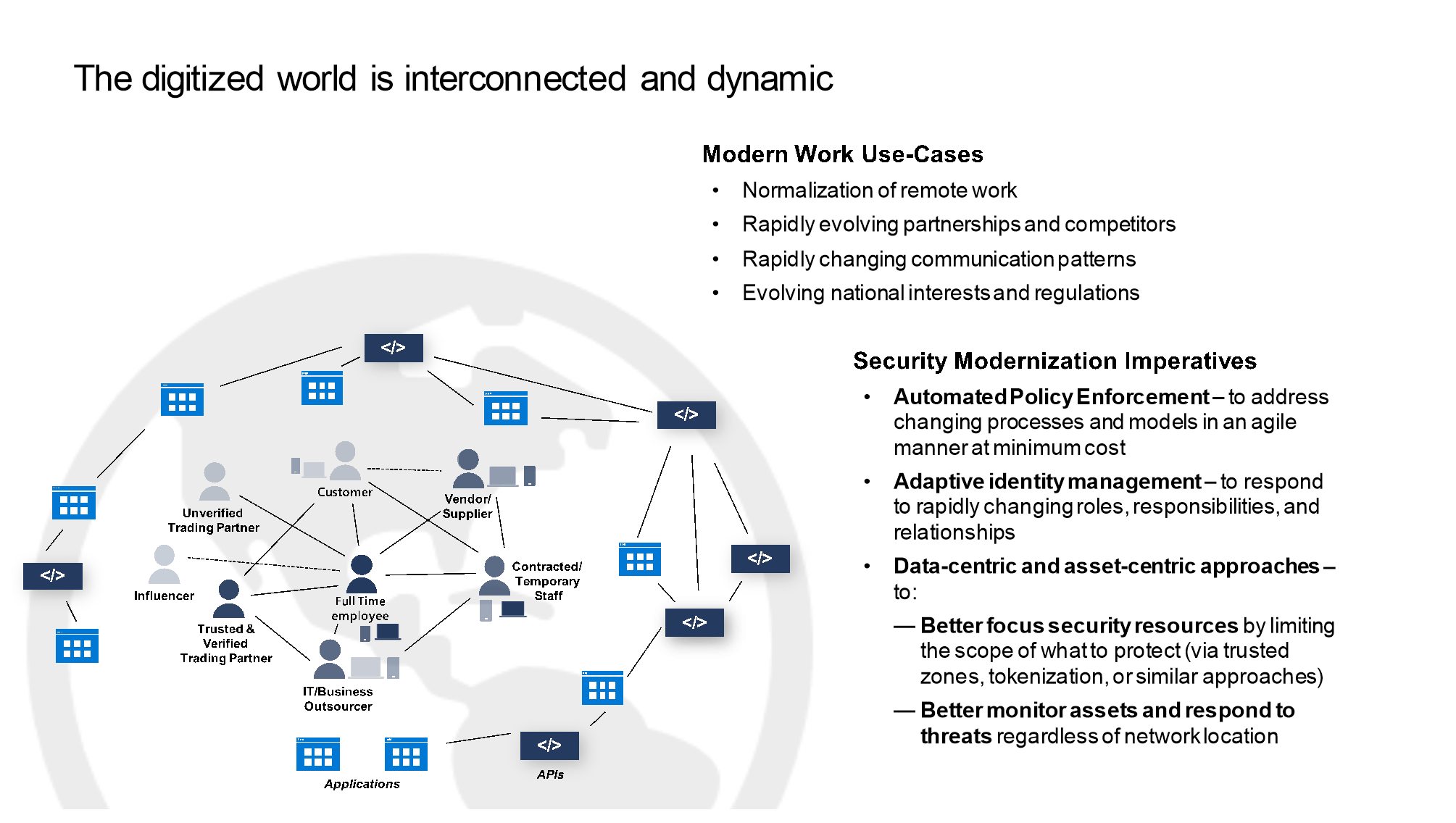
Getting Started with Zero Trust in Your Organization

Embarking on a Zero Trust 5G Security environment involves manageable steps:
- Assessment: Evaluate current security posture and identify priority assets.
- Strategy Development: Formulate a phased implementation roadmap aligned with business risks and priorities.
- Pilot Implementation: Launch a focused pilot to demonstrate value and refine strategies.
- Expansion and Integration: Gradually scale Zero Trust principles throughout your organization’s digital ecosystem.
Origo supports your journey at every phase, ensuring successful outcomes aligned with both security and operational objectives.
Conclusion
As enterprises increasingly adopt cloud-native 5G technologies, implementing a robust Zero Trust architecture becomes essential to mitigate new risks effectively. By taking a human-centered approach, Origo ensures your Zero Trust strategy not only safeguards critical assets but also enhances your workforce’s productivity and satisfaction.
Contact Origo today and learn how we can partner with your organization to implement Zero Trust principles that secure your future in the rapidly evolving 5G landscape.

Contact us today to learn how we can help you implement Zero Trust principles in ways that strengthen security while enhancing productivity and user satisfaction. Contact us today and start your journey toward secure, human-centered Zero Trust architecture with Origo.
info@origo.ec